Research & Innovation

The ELASTIC architecture includes five key blocks for tackling the challenges of secure and resource-efficient service orchestration for 6G networks. The Management & Orchestration block manages services across cloud-fog-edge infrastructures, enhancing scalability and security. The Isolation block protects data from Wasm and eBPF tools using Trusted Execution Environment and hardware abstraction frameworks. The Communication block ensures secure, efficient data exchange between tools, encryption, and accelerated microservices. The Monitoring & Detection block provides continuous, efficient security monitoring and cybersecurity issue reporting. The Trust & Access Control block ensures authorised access to sensitive data through remote attestation platforms.
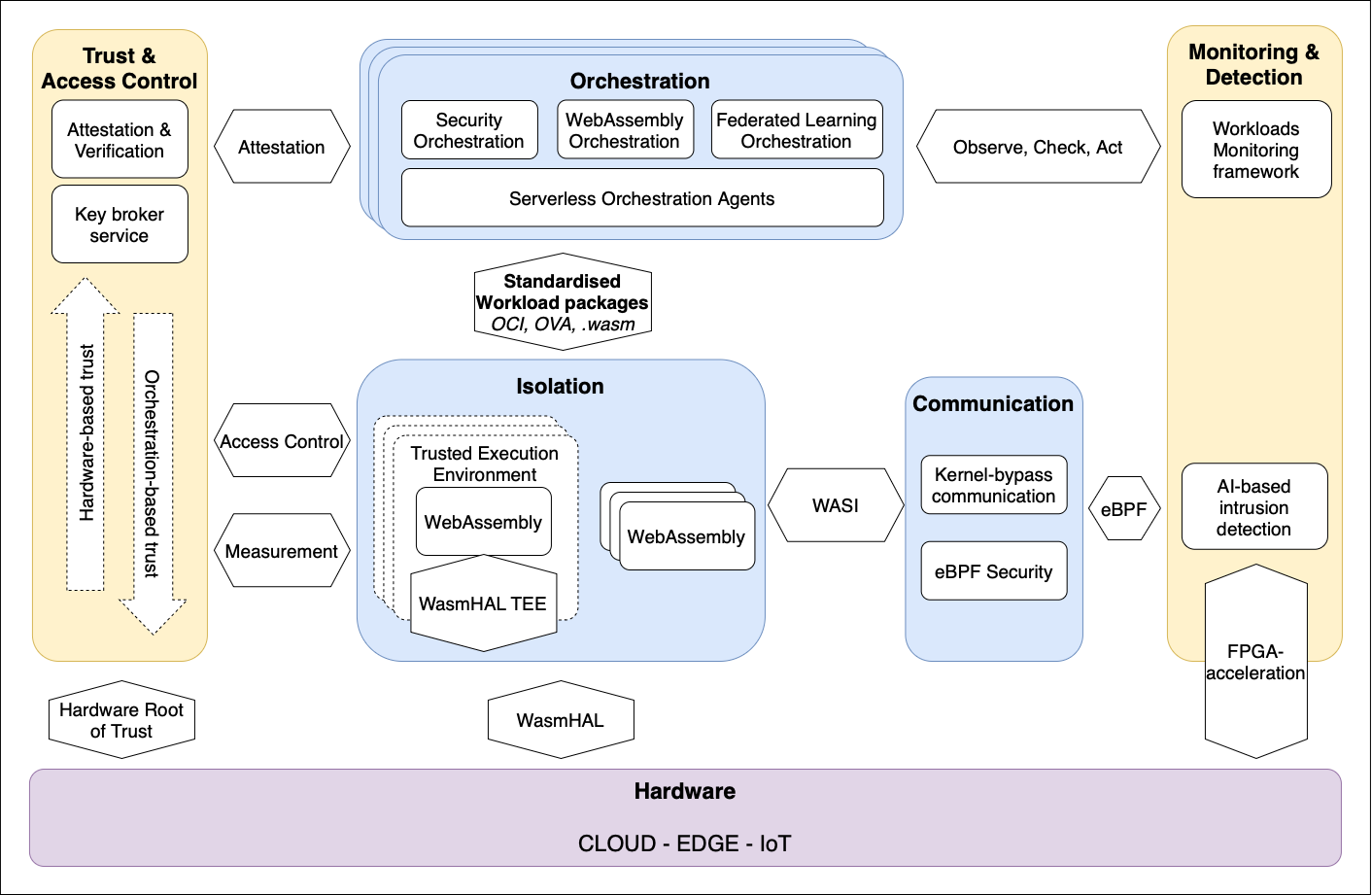
Management & Orchestration
The orchestration block within the ELASTIC project is designed to manage services across diverse cloud-fog-edge infrastructures, enhancing scalability, flexibility, and security. It aims to optimize the deployment and coordination of workloads across these distributed environments, enabling resource-efficient and secure service delivery. By leveraging advanced technologies, like WebAssembly (Wasm), Federated Learning, and Trusted Execution Environments (TEEs), the orchestration block supports dynamic and automated service management improving the efficiency of edge devices and the overall infrastructure. This approach ensures scalable, reliable, and secure solutions that meet the challenges of modern and resource-constrained environments.
Below, we introduce the components that participate in this block, along with their innovations and impact.
Federated Learning as a Service (FLaaS) (TID)
- TRL Start-End: 4 → 6
- Description: TID has developed FLaaS, enabling seamless Federated Learning (FL) model building on user devices, facilitating collaboration to create joint models without centralized data. It will extend FLaaS with Split Learning (SL) for more efficient training on resource-constrained devices.
- Innovation: FLaaS will integrate new algorithms to optimize communication, computation costs, and heterogeneous device support, alongside theoretical guarantees for client-helper assignment and scheduling, improving training efficiency.
- Impact: By enabling resource-constrained edge devices to contribute to model training, FLaaS advances Federated AI orchestration, contributing to more efficient and scalable AI solutions in real-world applications.
Wasm-operator (IMEC)
- TRL Start-End: 3 → 4
- Description: This project provides a runtime for running Kubernetes operators in WebAssembly (Wasm), improving memory usage in Kubernetes clusters by reducing the overhead of traditional containerization.
- Innovation: The prototype reduces memory consumption by running operators in a shared Wasm runtime, swapping operators to disk when idle, and using Rust for better efficiency.
- Impact: It enhances Kubernetes orchestration, making it more resource-efficient, especially on edge devices, thus improving scalability and performance for resource-constrained environments in ELASTIC.
Light-weight Security Orchestrator for Edge Devices (THS)
- TRL Start-End: 2 → 4
- Description: This agent orchestrates security functions via WebAssembly (WASM) workloads, integrating with Trusted Execution Environments (TEEs) to ensure secure service deployments across cloud and edge infrastructures.
- Innovation: It dynamically adapts security policies, enforces remote attestation for trusted environments, and continuously monitors workloads to adjust security measures in real
- Impact: It provides a flexible and automated security framework for edge devices, ensuring continuous compliance and resilience against evolving security threats.
Federated Learning Toolbox (ZEN)
- TRL Start-End: 3 → 4
- Description: This toolbox facilitates secure, privacy-preserving collaborative ML across distributed datasets, enabling Federated Learning (FL) on devices (including resource-constrained edge nodes) using Wasm.
- Innovation: It pioneers secure FL orchestration on Wasm and supports encrypted computation within popular ML frameworks.
- Impact: It ensures enhanced security, prevents unauthorized data access, and optimizes runtime performance by leveraging Wasm’s sandboxed execution model on edge nodes, enabling scalable AI for IoT networks.
TEE Software Management Agent (UVC)
- TRL Start-End: 2 → 3
- Description: The TEE Agent ensures secure workload management within a Trusted Execution Environment (TEE), validating integrity and managing cryptographic keys and access control.
- Innovation: It integrates remote attestation, cryptographic management, and workload monitoring into a unified framework that secures data throughout its lifecycle within TEEs.
- Impact: It strengthens ELASTIC’s security framework by safeguarding sensitive data and ensuring trusted execution in edge devices, making it essential for compliance and data protection in sensitive environments.
Reliable Enclave Migration Protocols (AAL)
- TRL Start-End: 3 → 4
- Description: This protocol enables secure migration of resources between hosts in an ELASTIC-based system, ensuring data integrity and availability even in adversarial conditions.
- Innovation: By utilizing distributed algorithms like consensus or fair exchange, it ensures atomic migration and handles network interruptions without compromising security.
- Impact: It enhances the reliability and security of distributed systems, allowing seamless migration in edge computing environments, crucial for maintaining continuity in ELASTIC’s operations.
Propeller Orchestrator (AMA)
- TRL Start-End: 1 → 4
- Description: Propeller is a lightweight, modular orchestrator for deploying WebAssembly (Wasm) workloads across the full Cloud-Edge-IoT continuum – from high-performance servers to microcontrollers running real-time operating systems (RTOS). It is designed to enable secure, low-latency, event-driven Function-as-a-Service (FaaS) execution, even on resource-constrained devices.
- Innovation: Propeller eliminates dependencies on heavyweight orchestration platforms like Kubernetes, introducing a new class of Wasm-native, cloud-to-IoT orchestration. Its architecture integrates scheduling (Manager), lightweight execution agents (Proplets), OCI-compliant module retrieval, and secure multi-protocol messaging (SuperMQ), enabling unified workload management with minimal overhead.
- Impact: As a core enabler in ELASTIC, Propeller supports native orchestration of 6G IoT data fabric services (Demonstrator 1) and secure workload migration across trust domains (Demonstrator 2). It addresses critical gaps in scalability, flexibility, and efficiency for Wasm orchestration in heterogeneous infrastructures, setting a foundation for secure real-time applications at the edge.
- Repository: https://github.com/absmach/propeller
- Documentation: https://docs.propeller.abstractmachines.fr/
Isolation
The Isolation block within the ELASTIC project focuses on securing data and workloads by utilizing Trusted Execution Environments (TEEs) and hardware abstraction frameworks. This block is designed to protect data from WebAssembly (Wasm) and eBPF tools, ensuring that sensitive information remains isolated from potential threats during execution. Leveraging TEEs, Secure Elements, and automated security tooling guarantees that data confidentiality and integrity are maintained even in distributed and resource-constrained environments. This approach enables secure, privacy-preserving computation across cloud, fog, and edge infrastructures, reinforcing ELASTIC’s commitment to building resilient and secure systems.
The following components contribute to this block, each with their own innovations and impact.
Data Protection at Rest at the Edge with TEE Solution (THS)
- TRL Start-End: 2 → 4
- Description: Thales (THS) develops a component to secure data at rest originating from WebAssembly (WASM) workloads running inside Trusted Execution Enclaves (TEEs). The solution uses hardware-secured cryptographic keys, stored within a root of trust, to transparently encrypt the data with minimal performance overhead.
- Innovation: This solution combines the flexibility of WASM with the high security of TEEs, providing a transparent and efficient encryption process. By leveraging Secure Elements as physical roots-of-trust, it ensures secure, platform-agnostic handling of sensitive data in edge computing environments.
- Impact: The component ensures enhanced data confidentiality and security, meeting the growing need for secure data storage in edge environments. This aligns with the ELASTIC project’s goal of enabling secure infrastructures for sensitive workloads, contributing to privacy and data protection across distributed systems.
WasmHAL-Trust: Automation Tooling for Confidential Computing Environments (LUN)
- TRL Start-End: 2 → 4
- Description: WasmHAL-Trust extends the functionality of WebAssembly by providing a secure, WASI-compliant interface for executing workloads in confidential container platforms. It automates the integration of TEE-based platforms with WASM workloads, enabling secure execution across multiple environments.
- Innovation: The component provides a reference implementation for adapting TEE platforms to WebAssembly, focusing on privacy-preserving, multi-stakeholder, secure execution of workloads. This integration simplifies secure workload execution across diverse environments.
- Impact: WasmHAL-Trust supports the adoption of confidential computing by ensuring secure, portable execution of workloads. This plays a crucial role in ELASTIC’s goal of delivering a flexible, multi-platform infrastructure for secure computing.
WASI Security (IMEC)
- TRL Start-End: 2 → 4
- Description: WASI Security provides a standardized way to define and enforce security policies for WebAssembly workloads. It bridges WebAssembly runtimes and higher-level orchestrators, enabling policy-driven security management.
- Innovation: This component introduces a unified security policy format that is applicable across different WebAssembly runtimes. It allows consistent, scalable, and automated enforcement of security measures.
- Impact: By standardizing security policies, WASI Security enhances consistency and ease of security management for WebAssembly-based applications. It ensures that workloads across various platforms can securely interact, contributing to ELASTIC’s overall security strategy.
Automatic MAC Profiles for Wasm Runtime Containers (LUN)
- TRL Start-End: 3 → 4
- Description: This tool automates the creation of Mandatory Access Control (MAC) profiles using AppArmor for WebAssembly applications running on Docker, ensuring that only the necessary privileges are granted to workloads. It supports any WebAssemby runtime running on Docker.
- Innovation: It offers a unique automation capability that generates MAC profiles based on workload requirements, reducing human error and ensuring the principle of least privilege. This automation reduces the attack surface by limiting access to essential resources.
- Impact: By automating the creation of MAC profiles, this tool improves security while simplifying access management for WebAssembly applications. This approach minimizes security risks and increases overall system resilience, supporting ELASTIC’s security framework.
WasmHAL Hardware, Interfaces, and Runtime Extensions (IMEC)
- TRL Start-End: 2 → 4
- Description: This component extends the WebAssembly (WASM) ecosystem to support secure hardware interactions through IoT protocols such as USB, I2C, and GPIO. It provides a secure SDK and interfaces that enable WebAssembly applications to communicate with edge devices, bridging the gap between cloud and edge computing.
- Innovation: By extending the WASI standard, this solution enables WebAssembly applications to interact with physical devices in IoT environments. This interaction opens up new possibilities for resource-constrained devices in edge scenarios.
- Impact: The ability to securely interface with hardware in edge environments enhances WebAssembly’s utility in IoT applications. This development strengthens the ELASTIC project’s vision for secure, scalable, and interoperable edge computing infrastructures.
Static eBPF Code Security Analyzer (POLITO)
- TRL Start-End: 2 → 3
- Description: The Static eBPF Code Security Analyzer is a tool designed to analyze eBPF C code for potential security vulnerabilities. It provides developers with clear, actionable error messages and suggestions for fixing identified issues before deployment.
- Innovation: By integrating security analysis early in the development process, the tool helps developers identify security flaws in eBPF programs before they become a problem. This improves the overall security of eBPF-based systems.
- Impact: The analyzer enhances productivity and security by enabling early detection of vulnerabilities, reducing the risk of issues in deployed eBPF programs. This contributes to a more secure deployment of eBPF programs, aligning with ELASTIC’s goals of secure orchestration in next-gen computing environments.
Communication
The Communication block within the ELASTIC project ensures secure, efficient, and high-performance data exchange between the integrated tools, encryption systems, and microservices. By leveraging advanced technologies like WebAssembly (Wasm), eBPF, and RDMA, this block optimizes communication speed, reduces latency, and supports secure data transfer across edge, fog, and cloud environments. It plays a vital role in enabling low-latency, high-throughput orchestration of Function-as-a-Service (FaaS) workloads, ensuring that ELASTIC’s platform is both secure and scalable for next-gen computing.
The components featured in this block, along with their innovations and impact, are outlined below.
Static Analysis of Interaction Between Wasm Modules (AAL)
- TRL Start-End: 1 → 2
- Description: This component aims to enhance the performance and security of WebAssembly (WASM) systems by analysing the interactions between different components to ensure that larger distributed systems behave as expected and with greatest efficiency.
- Innovation: By analyzing component code and metadata, this tool identifies potential redundancies and opportunities for optimization in modular WASM applications. It also facilitates the verification of composable systems, extending existing attestation tools like Veraison to support bundles of multiple attestations.
- Impact: By analyzing the components, this tool identifies potential redundancies and opportunities for optimization in modular WASM applications. It also facilitates the verification of composable systems by that produce bundles of attestations that apply only to small parts of the overall system.
Accelerated Microservices Interconnection (POLITO)
- TRL Start-End: 1 → 4
- Description: This component seeks to accelerate communication between microservices by bypassing traditional software network stack limitations. Using technologies like eBPF, it aims to minimize network overhead and enhance communication speed within and between containerized applications.
- Innovation: The solution employs techniques like socket splicing and shared memory to speed up application-to-application data transfers within hosts. It also explores using eBPF and RDMA for improving communication throughput across physical networks, bypassing the standard network stack for local and remote microservice interactions.
- Impact: By drastically improving inter-service communication performance, this component supports ELASTIC’s mission to build a fast, secure, and scalable orchestration platform for Function-as-a-Service (FaaS) workloads, reducing latency and increasing throughput in distributed environments.
eBPF Distributed State Synchronisation (POLITO)
- TRL Start-End: 1 → 4
- Description: This component develops methods for efficient state sharing and consensus within a distributed computing cluster. Using eBPF and RDMA, it aims to reduce communication latency and improve the synchronization of distributed state, achieving ultra-low latency (under 100 microseconds).
- Innovation: By extending eBPF map types to replicate state across distributed systems, this component enables seamless data synchronization across multiple servers. It also includes the development of leader election and consensus algorithms to ensure reliable, high-performance state management in ELASTIC’s FaaS infrastructure.
- Impact: This innovation facilitates faster, more reliable communication between distributed blocks of the ELASTIC architecture. It enables real-time data synchronization across distributed environments, improving performance and scalability of edge and cloud-based systems in ELASTIC’s platform.
Monitoring & Detection
The Monitoring & Detection block within the ELASTIC project ensures continuous, efficient security monitoring and cybersecurity issue reporting for edge, fog, and cloud infrastructures. This block leverages cutting-edge technologies like eBPF, AI-based intrusion detection, and hardware-based cryptography to detect vulnerabilities, monitor network activity, and respond to threats in real time. It plays a crucial role in maintaining ELASTIC’s security integrity and resilience by providing continuous visibility, enhancing threat detection, and ensuring the rapid resolution of issues across distributed systems.
The key components of this block, showcasing their innovations and the impact they bring are listed below.
NETTO - A Tool to Measure the Cost of the Linux Network Stack in Real-Time (POLITO)
- TRL Start-End: 3 → 4
- Description: NETTO is a tool designed to measure CPU overhead for network functions on Linux hosts, leveraging eBPF to capture stack traces with minimal impact on system performance. It efficiently monitors the Linux network stack, providing insights into areas requiring optimization.
- Innovation: NETTO innovates by using a sampling-based profiler instead of direct measurement, ensuring minimal overhead while maintaining detailed metric granularity. This approach enables continuous monitoring of the network stack with very low resource consumption.
- Impact: NETTO will provide valuable real-time monitoring for ELASTIC’s networking components, helping to identify performance bottlenecks in network processing and enabling informed optimization of ELASTIC’s networking stack, improving efficiency and responsiveness.
Hardware-based Cryptography Module (TUC)
- TRL Start-End: 2 → 3
- Description: This cryptography module leverages hardware-accelerated platforms, like FPGAs and GPUs, to perform advanced cryptographic operations, enabling real-time encryption, authentication, and integrity protection within ELASTIC’s network infrastructure.
- Innovation: The module enhances cryptographic efficiency and adaptability in real-time applications by integrating hardware acceleration with open-source cryptographic framework. Additionally, it supports dynamic cryptographic techniques, ensuring robust data security while maintaining high system performance.
- Impact: The integration of the cryptography module into ELASTIC strengthens the security of sensitive data and network communications, particularly in 6G environments. It enhances system resilience against cyberattacks, aligning with ELASTIC’s objectives for secure and scalable network operations.
Artificial Intelligence Intrusion Detection/Prevention System (TUC)
- TRL Start-End: 3 → 4
- Description: This tool integrates artificial intelligence (AI) with a hardware-accelerated Intrusion Detection System (IDS), utilizing the Aho-Corasick algorithm for high-speed and efficient pattern matching to identify security threats in real time.
- Innovation: The system offers adaptive threat detection, enhancing its capability to identify emerging cyber threats by incorporating AI-driven frameworks. It operates on reconfigurable hardware, ensuring high-performance intrusion detection while dynamically adapting to new attack vectors.
- Impact: By improving the scalability and intelligence of intrusion detection, this system enhances ELASTIC’s security posture, offering real-time protection for network operations against evolving cyber threats and ensuring continuous, efficient monitoring of ELASTIC’s infrastructure.
Mobility Attack Robust IoT Resource Allocation Model (LUN)
- TRL Start-End: 2 → 4
- Description: This model uses AutoML to create robust mobility prediction models for IoT networks, ensuring correct resource allocation even in the presence of adversarial attacks that disrupt traditional prediction systems.
- Innovation: The use of AutoML allows for dynamic retraining of mobility models, ensuring they remain resilient to adversarial behaviors. By adapting to malicious mobility patterns, it provides accurate resource allocation predictions without compromising performance.
- Impact: This innovation ensures that ELASTIC can maintain accurate and secure IoT resource management even under attack, improving network efficiency and resilience. It enables ELASTIC to offer robust mobility prediction services, which are vital for the secure operation of next-gen networks.
Observability Framework for Serverless Workloads (ERF)
- TRL Start-End: 1 → 3
- Description: This framework enables observability of WebAssembly-based serverless workloads in Kubernetes, using eBPF to collect detailed network data for monitoring and dynamic decision-making.
- Innovation: The framework is designed to support serverless workloads, offering near-real time monitoring via eBPF hooks, enabling data collection for network performance analysis. The focus on WebAssembly allows integration with diverse application types in modern cloud environments.
- Impact: The observability framework will provide ELASTIC with enhanced visibility into the behavior of serverless workloads, facilitating better performance tuning and more responsive system management. It will enable dynamic monitoring, improving the overall reliability and performance of ELASTIC’s serverless infrastructure.
Trust & Access Control
The Trust & Access Control block in ELASTIC guarantees secure, authorized access to sensitive data and workloads through advanced remote attestation platforms. It combines multiple technologies, such as Trusted Execution Environments (TEEs) and fine-grained access control solutions to ensure that only trusted entities can access critical resources. This block establishes a secure foundation for ELASTIC’s infrastructure by verifying system integrity, enforcing secure key management, and enabling scalable access control in distributed environments.
Below are the components involved in this block, along with a description of their innovations and impact.
Remote Attestation Platform (THD)
- TRL Start-End: 2 → 4
- Description: The Remote Attestation Platform ensures the integrity and security of a system by verifying the health of software components running in confidential computing enclaves. It checks that workloads are running in a secure environment and uses a hardware-based Root of Trust to measure and verify the system’s integrity. ELASTIC’s platform will introduce an abstraction layer to ensure compatibility across various confidential computing technologies.
- Innovation: The innovation lies in creating an abstraction layer that supports multiple hardware technologies and enhances the security of multi-tenant and distributed systems. ELASTIC will implement lightweight, efficient protocols to overcome current challenges with secure workload migration and ensure robust remote attestation.
- Impact: This platform contributes to the security of ELASTIC by enabling secure and trusted attestation in multi-cloud and distributed environments. It ensures that workloads running in confidential computing environments remain secure, even during migration, and facilitates secure multi-party computation in distributed systems.
Key Broker Service (THD)
- TRL Start-End: 2 → 4
- Description: The Key Broker Service plays the role of a relying party in the attestation process, verifying the integrity of virtual machines (VMs) in a Trusted Execution Environment (TEE) before provisioning secret keys. It supports a secure key management system that protects software images throughout their lifecycle, ensuring confidentiality and integrity.
- Innovation: This service allows for the separation of duties between cloud providers and customers by enabling them to manage their own keys (BYOK/HYOK). It ensures end-to-end confidentiality protection of software images, only decrypting them once the attestation is verified.
- Impact: By integrating this service, ELASTIC can guarantee that software images remain secure during migration to the cloud, protecting against tampering. It enhances the security of confidential workloads and ensures that key provisioning is tightly controlled and secure after a successful attestation.
Multi-platform Attestation Component (ERF)
- TRL Start-End: 2 → 3
- Description: This component enables verification of attestation evidence from multiple platforms via a unified interface based on the WebAssembly component model. It provides tools for entities to verify trust across different TEEs and supports attestation of data producers and consumers within ELASTIC’s Data Fabric.
- Innovation: The innovation lies in its ability to dynamically load WebAssembly components for verifying evidence from various platforms, enabling attestation across multiple TEE types and vendors. This flexibility enhances interoperability and simplifies the verification process in heterogeneous environments.
- Impact: This component will improve trust in the ELASTIC architecture by allowing seamless attestation verification across different platforms. It enables data producers and consumers within the ecosystem to trust the integrity of workloads, contributing to a secure and trustworthy environment for ELASTIC’s services..
Light-weight Attribute-based Access Control (ABAC) Solution (THS)
- TRL Start-End: 3 → 4
- Description: The ABAC solution enforces fine-grained access control policies for WASM containers in resource-constrained environments like Edge Computing. It integrates with ELASTIC’s workload identity framework, ensuring secure and authenticated interactions between workloads and their environment.
- Innovation: This component introduces a lightweight approach to ABAC, ensuring it operates efficiently on embedded platforms with limited resources. It also incorporates capability-based access control (CBAC) to maintain security even when the central control plane is unavailable due to disruptions.
- Impact: WASI Flexibly-defined Capabilities will enhance the security of ELASTIC’s WASM-based workloads by enabling finer-grained, runtime-enforced access control policies. This ensures that resource interactions are securely managed, reducing the risk of unauthorized access and improving the overall security posture of ELASTIC’s edge computing environment.
WASI Flexibly-defined Capabilities (AAL)
- TRL Start-End: 1 → 3
- Description: The WASI Flexibly-defined Capabilities component enables dynamic, domain-specific access control for WASM applications. It allows custom security policies to be applied to resources, ensuring that only authorized actions are performed on specific resources based on flexible, runtime-enforced restrictions.
- Innovation: This component innovates by extending existing WASI interfaces with custom, flexible capabilities that can be dynamically applied to resources. It allows the enforcement of complex access control policies tailored to specific application needs without compromising performance or flexibility.
- Impact: WASI Flexibly-defined Capabilities will enhance the security of ELASTIC’s WASM-based workloads by enabling precise, runtime-enforced access control policies. This ensures that resource interactions are securely managed, reducing the risk of unauthorized access and improving the overall security posture of ELASTIC’s edge computing environment.
